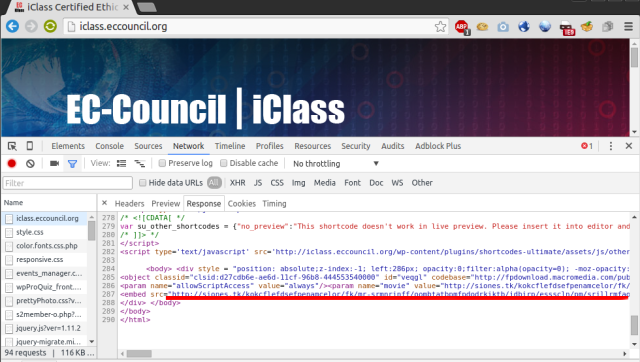
 Embedded code used in a drive-by attack on the website of EC-Council, the professional organization that maintains the Certified Ethical Hacker program. Fox IT
Embedded code used in a drive-by attack on the website of EC-Council, the professional organization that maintains the Certified Ethical Hacker program. Fox IT For the past four days, including during the hour that this post was being prepared on Thursday morning, a major security certification organization has been spreading TeslaCrypt malware—despite repeated warnings from outside researchers.
EC-Council, the Albuquerque, New Mexico-based professional organization that administers the Certified Ethical Hacker program, started spreading the scourge on Monday. Shortly afterward, researchers from security firm Fox IT notified EC-Council officials that one of their subdomains—which just happens to provide online training for computer security students—had come under the spell of Angler, a toolkit sold online that provides powerful Web drive-by exploits. On Thursday, after receiving no reply and still detecting that the site was infected, Fox IT published this blog post, apparently under the reasonable belief that when attempts to privately inform the company fail, it's reasonable to go public.
Like so many drive-by attack campaigns, the one hitting the EC-Council is designed to be vexingly hard for researchers to replicate. It targets only visitors using Internet Explorer and then only when they come to the site from Google, Bing, or another search engine. Even when these conditions are met, people from certain IP addresses—say those in certain geographic locales—are also spared. The EC-Council pages of those who aren't spared then receive embedded code that redirects the browser to a chain of malicious domains that host the Angler exploits.
The Fox IT blog post continued:
Through this embedding the client is redirected a couple of times to avoid/frustrate/stop manual analysis and some automated systems. Once the user has jumped through all the redirects he/she ends up on the Angler exploit kit landing page from which the browser, flashplayer plugin or silverlight plugin will be exploited. The Angler exploit kit first starts the 'Bedep' loader on an exploited victim machine which will download the final payload.
The way the redirect occurs on the EC-COUNCIL website is through PHP code on the webserver which is injecting the redirect into the webpage. A vulnerability in the EC-COUNCIL website is most likely exploited as it runs the very popular WordPress CMS which has been a target through vulnerable plug-ins for years.
Payload details: TeslaCrypt
This specific campaign instance of the Angler exploit kit drops 'TeslaCrypt' on the exploited victim's machine. TeslaCrypt is a piece of ransomware which takes a victim's files hostage with the use of encryption. Once the victim's files have been successfully encrypted a ransom note is presented to instruct the victim on ways to recover files:
 Enlarge
Enlarge TeslaCrypt requires the victim to pay around 1.5 BTC to get their files back; this equals to approximately 622$ at the current conversion rate.
Further Reading Big-name sites hit by rash of malicious ads spreading crypto ransomware [Updated]
Big-name sites hit by rash of malicious ads spreading crypto ransomware [Updated] New malvertising campaign may have exposed tens of thousands in the past 24 hours.
The EC-Council infection comes eight days after The New York Times, the BBC, and other big-name Web publishers fell victim to a rash of malicious ads that attempted to surreptitiously install crypto ransomware and other malware on the computers of unsuspecting visitors. Last week's campaign was unusual for hitting so many different ad networks all at once. So far, none of the compromised networks—including those run by Google, AppNexis, AOL, and Rubicon—have provided statements explaining how the mass compromise happened or what they've done to ensure that similar attacks won't succeed again.Source: Certified Ethical Hacker website caught spreading crypto ransomware
No comments:
Post a Comment