This entry was posted in General Security, Wordfence, WordPress Security on December 16, 2016 by mark 49 Replies
At Wordfence we constantly monitor the WordPress attack landscape in real-time. Three weeks ago, on November 24th, we started seeing a rise in brute force attacks. As a reminder, a brute force attack is one that tries to guess your username and password to sign into your WordPress website.
In today's post we show you how attacks have increased during the past 3 weeks and share some data about where attacks are originating from.
First: How to protect yourself from these attacksBrute force attacks are unsophisticated. They are simple password guessing attacks. A machine will automatically try to sign into your website over and over in the hope that it can guess your password.
If you install the free version of Wordfence, you are automatically protected against brute force attacks. It's that simple. We also automatically block the worst offenders completely, and we share some information below on who those are.
We have a few other really cool options, like preventing username discovery and immediately locking out invalid usernames. All these techniques help protect you against brute force attacks.
Download and install the free version of Wordfence today to get instant protection against brute-force attacks.
A sustained increase in Brute Force WordPress AttacksDuring the past three weeks we have seen the number of sites attacked each day almost double. The dotted blue line indicates the average number of attacked sites for the 60 days shown. The charts below show attack patterns over the past 2 months.

We have observed the number of brute force attacks blocked increase significantly above our 60 day average.
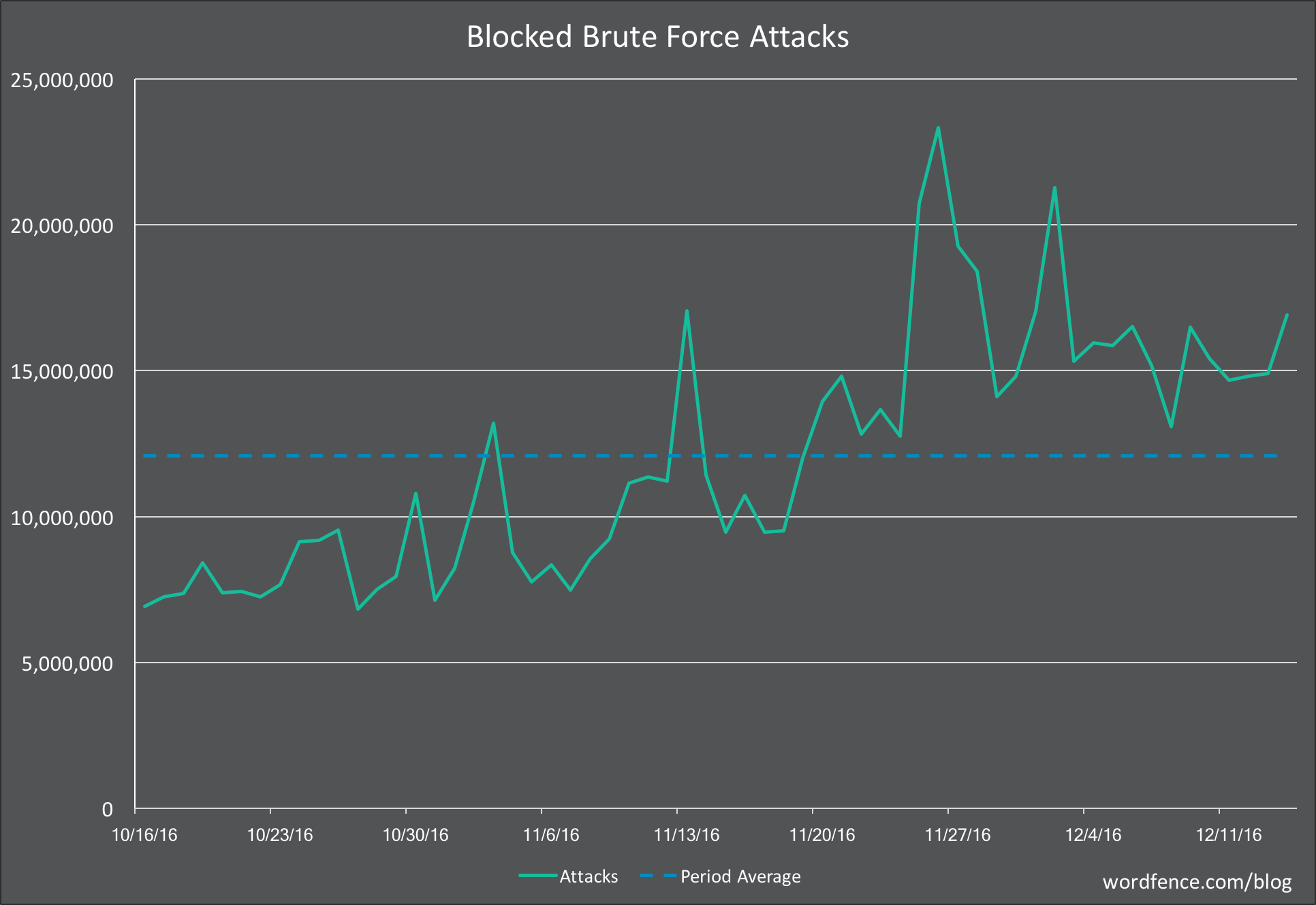
And what most concerns us is that we have seen a rise in unique IP addresses that are attacking WordPress websites per day. This rise started on November 24th and has spiked significantly during the past week.
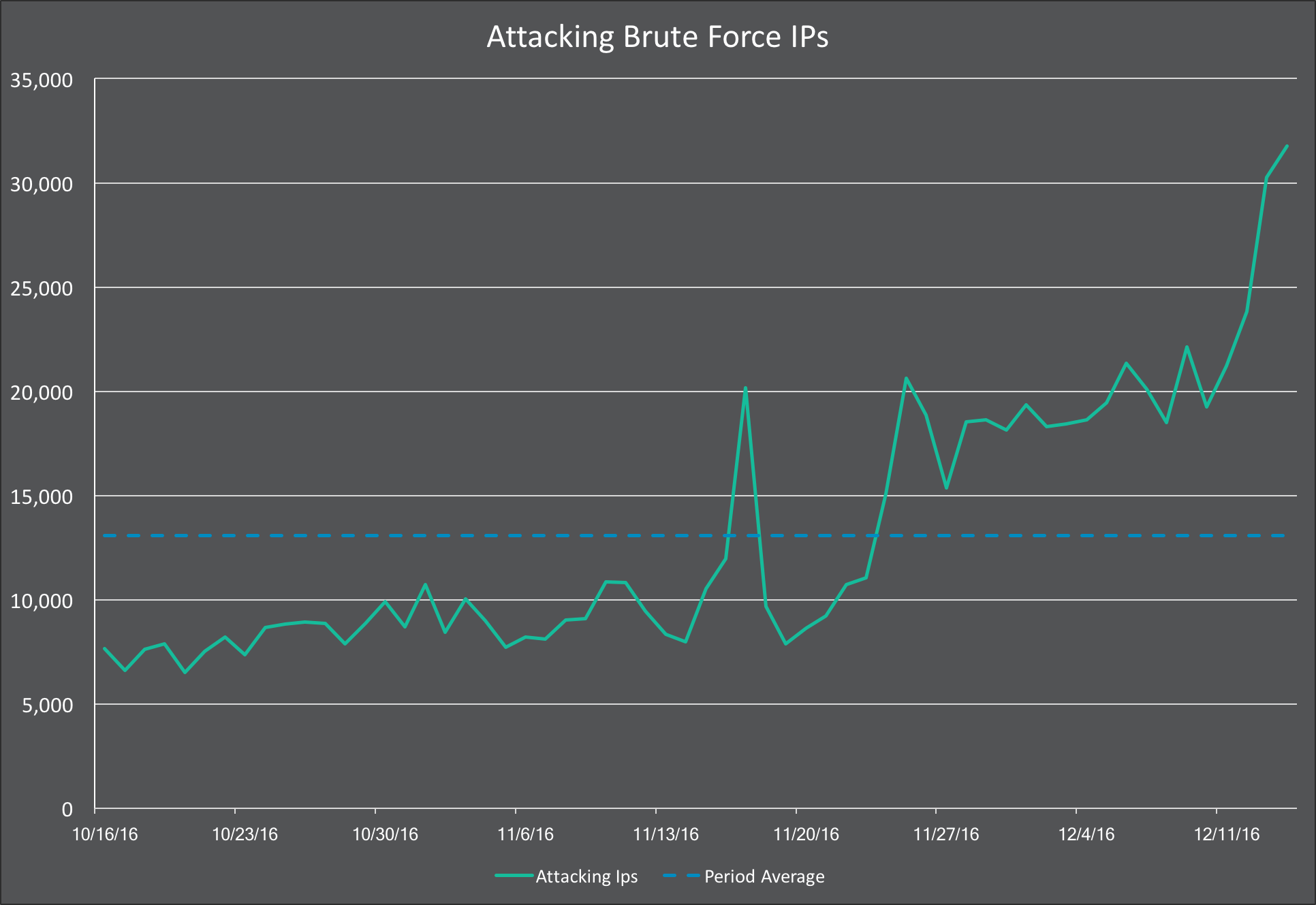
This has now increased far above our baseline. Usually we see an average of around 13,000 unique IP's attacking each day. We're currently seeing over 30,000 unique attacking IPs and this is continuing to increase.
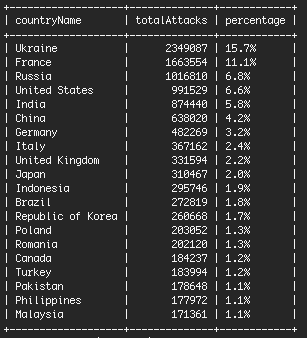
Who is Brute Force Attacking WordPress sites?The charts above show data for the past two months. We then analyzed attacks during the past 24 hours to see who is currently attacking WordPress sites.
The following table shows the top 20 countries sorted by attacks during the past 24 hours. As you can see, Ukraine is by far the main culprit, responsible for over 15% of total attacks. That is a lot when you consider that the population of Ukraine is only 45 million people.
Most of the attacks come from 8 IP addresses in Ukraine.
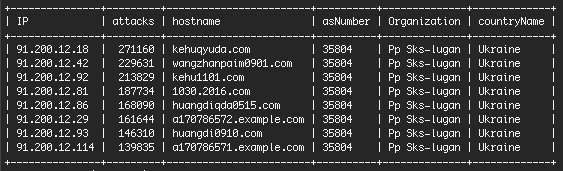
These IPs all belong to the same organization and are on the same network. Doing a Google search on the top IP brings back many reports of abuse around the Internet. They belong to a hosting company in Ukraine called "Pp Sks-lugan". The servers are a mix. Some aren't running any services. Others appear to be running Windows IIS web server.
These IPs are using brute force attacks exclusively. They don't launch any sophisticated attacks. They are hammering away at WordPress sites at a rate of over a quarter million login attempts each, in some cases, during a 24 hour period.
When we add up attacks during the past 24 hours and group by the organization that owns the attacking IP address, you can really see the impact that the Ukrainian host is having.
Keep in mind that as you look at the data below, some organizations like GoDaddy are very large. They actually make up a large percentage of total WordPress sites on the Net. And so before you call out a hosting provider for being 'insecure', you should consider their size and that it takes the operations team at each hosting provider some time to respond to a hacked site and take it offline.
We also think the table below illustrates how most attacks originate from specific networks that are relatively obscure.
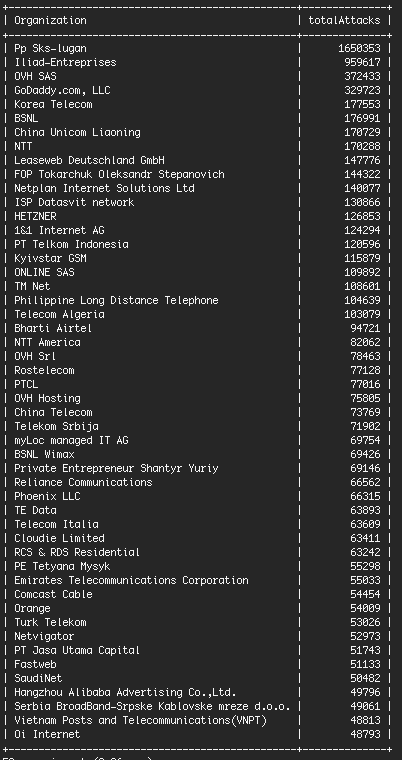
The top hosting provider is a tiny organization you've probably never heard of. But they're head and shoulders above most other companies on this list for the number of attacks that originate from their network.
The second company on the list, "Iliad-Entreprises", has 8 IP addresses in particular that launched between 50,000 and 210,000 attacks each during the past 24 hours. That is what makes up the bulk of the action on their network.
The difference between the top two networks and the network in third place is dramatic. OVH is a very large hosting provider, but we're seeing more than 4 times fewer attacks originating from their network than from the #1 Ukrainian host.
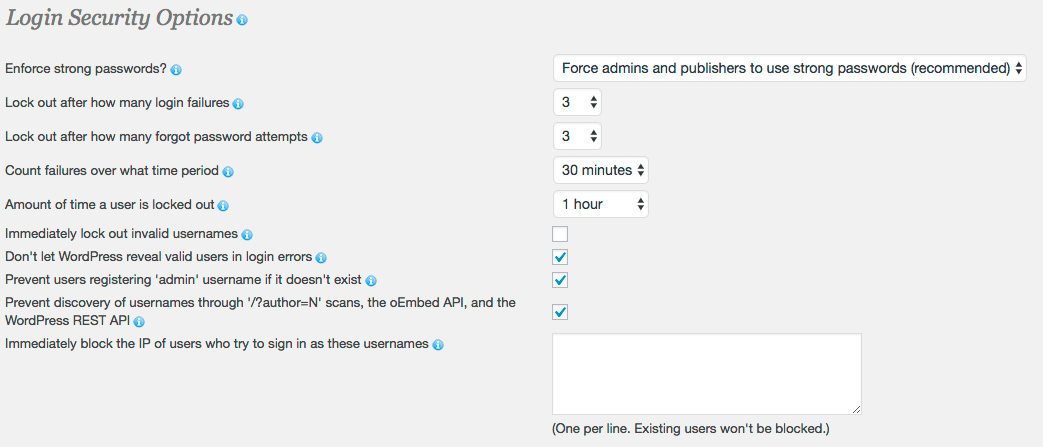
Lock it down and stay safe this holiday seasonIf you run a WordPress site, make sure you lock it down so that you can relax over the holiday season. Brute force attacks are easy to protect against if you have the right tools. I've included a screenshot below of the Wordfence Login Security options that give you an idea of the many different ways we stop brute force attacks in their tracks. Click for a larger image.
As always I would love to hear your feedback and comments below and will be around to respond.
Mark Maunder – Wordfence Founder/CEO
Thanks to Matt Rusnak and Dan Moen for their assistance editing this post.
Did you enjoy this post? Share it!
Source: Huge Increase in Brute Force Attacks in December and What to Do
No comments:
Post a Comment