This entry was posted in Research, WordPress Security on October 26, 2017 by Brad Haas 3 Replies
 During the last month, the information security media has paid a lot of attention to cryptocurrency mining malware. The Wordfence team has been monitoring the situation, and we are now starting to see attacks attempting to upload mining malware, and site cleaning customers that are already infected.
During the last month, the information security media has paid a lot of attention to cryptocurrency mining malware. The Wordfence team has been monitoring the situation, and we are now starting to see attacks attempting to upload mining malware, and site cleaning customers that are already infected.
In this post, you'll learn what cryptocurrency mining is, what's in it for the attackers, how to check if you have this issue and what to do about it if you do.
Cryptocurrency Mining Attacks on WordPressFor those of you who aren't up to speed, cryptocurrencies are digital currencies that can act as an alternative to traditional currencies. Examples include Bitcoin, Litecoin, Ethereum and Monero, among many others. Cryptocurrency mining is a computationally intense process that contributes to the operations of the cryptocurrency network while generating new currency. It takes a massive amount of computer resources to generate meaningful income. People interested in cryptocurrency mining generally need to invest in expensive equipment and solve for the power consumption and heat generated by hardware.
Recently online platforms have emerged that allow website owners to harness the computing power of their website visitors to mine cryptocurrency. Website owners simply sign up for an account and add some JavaScript to their site. The downside is that their visitors' experience is likely quite poor as their computer resources are then put to work mining. It is debatable whether website visitors will ever view this practice favorably, but it will be interesting to watch the trend evolve.
We saw the first attack on a WordPress site attempting to embed cryptocurrency mining code on September 17. Attack volume has been very low and unsophisticated so far. However, our Security Services Team is starting to see hacked websites with this malware, so the attackers are starting to have some success.
The attacks we have analyzed are all trying to exploit well-known security vulnerabilities that have been around for a long time; for example, the Gravity Forms exploit from mid-2016, or the Joomla com_jce exploit from early 2014. We have also seen quite a few attempts to insert mining code using compromised WordPress administrator accounts, as well as some attacks using compromised FTP accounts.
How Attackers Profit From Cryptocurrency Mining MalwareAttackers are embedding Javascript code from Coinhive on websites they have compromised. Coinhive provides a way to mine a cryptocurrency known as Monero. Monero differs from other cryptocurrencies like Bitcoin, in that it does not give miners who use GPUs or other specialized hardware a significant computational advantage. That means it is well-suited to use in web browsers, executing as JavaScript on consumer CPUs.
Site owners who place the Coinhive code on their websites earn Monero currency. The Coinhive code uses site visitors' computational resources to mine Monero. An attacker can place the Coinhive code on thousands of websites and earn Monero from the mining that happens in site visitors' browsers.
The following is an example of embedded Coinhive code that will mine Monero currency:
![]()
The research team at Checkpoint analyzed the profit potential for an attacker planting this malware. They concluded that an attacker successful enough to average 1,000 concurrent users across all infected sites would generate $2,398 in monthly revenue.
We think these attacks will grow in popularity very quickly given how lucrative they are. Attacks that attempt to embed cryptomining malware are currently unsophisticated, but we expect to see an increase in the sophistication of attacks as word gets out that this is a lucrative enterprise. We also expect these attacks to target higher-traffic websites, since the potential to profit increases greatly with higher numbers of concurrent site visitors.
How to Check if Your Site Is Infected With Cryptocurrency Mining MalwareThe Wordfence firewall blocks attacks attempting to infect sites with this malware. We have added detection capability to Wordfence for cryptominer scripts. This means that the scanner will warn you if it detects this type of script on your site. It also means that the Wordfence firewall will block any uploads that contain the script.
Wordfence Premium customers currently already have access to this detection capability. Free users will get access to this capability on November 24 via the Community version of the Threat Defense Feed.
It is important to make sure you detect an infection quickly if an attacker should manage to slip through your defenses. Below is an example of a scan finding that would indicate this infection exists on your site.
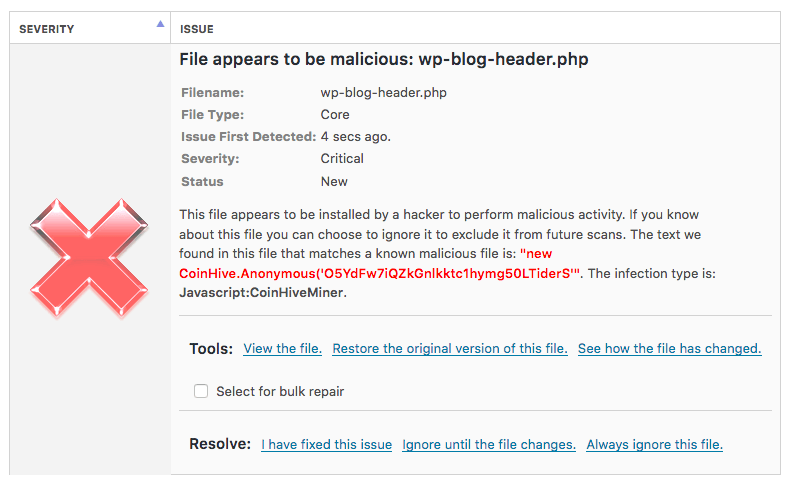
We have also added detection capabilities to Gravityscan. To run a scan on your site, simply go to the Gravityscan website and run a scan. For best results we recommend that you install the Gravityscan Accelerator.
Below is a scan finding example from Gravityscan.
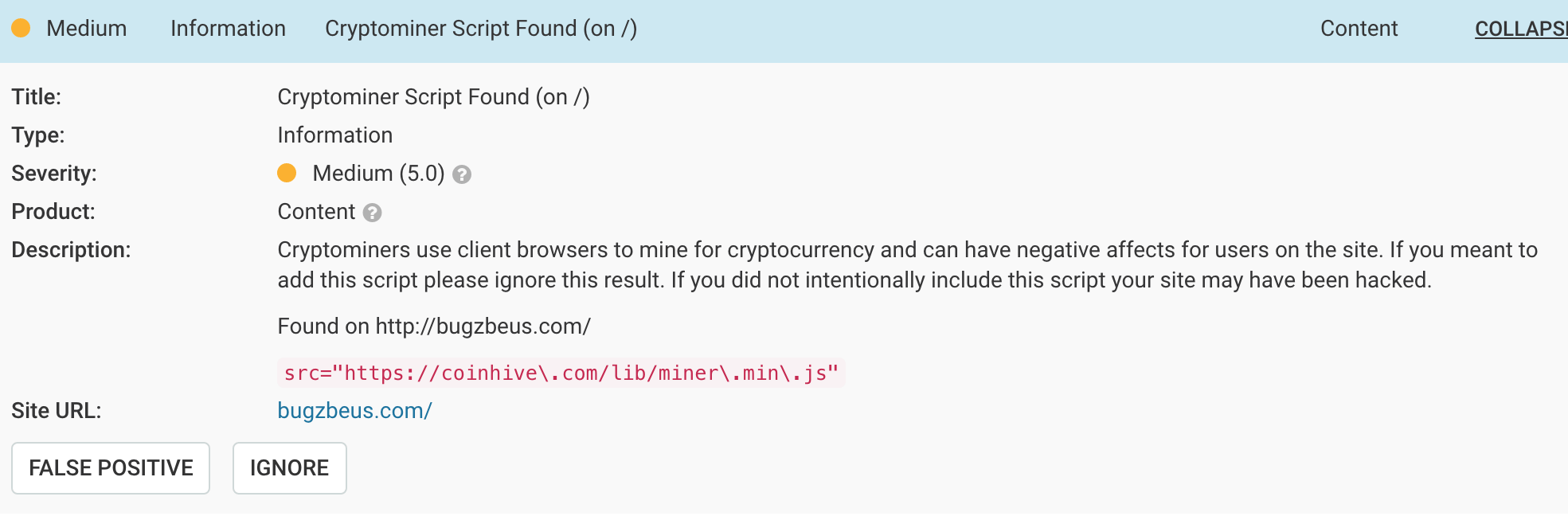
(If you have intentionally added a cryptominer script to your site, of course, you can simply ignore the finding on either platform.)
Some cryptomining malware may be more hidden or obfuscated, so always pay attention if many of your visitors start reporting poor performance by their browser or computer while visiting your site.
A few hackers have adjusted the miner settings so that it only uses only a portion of the available CPU power, or so that only one instance of the miner script can run at a time (even if it's open in multiple tabs).
![]()
But many of them are still set to use 100% of available resources, no matter what.
![]()
New business models are constantly emerging for attackers. Historically, attackers would use compromised websites to generate spam content or spam email. In the past decade, ransomware has gained popularity among attackers, as it allows them to extort money from victims. More recently, using stolen computational resources to mine cryptocurrency has emerged as a way for bad actors to profit from compromised systems.
This emerging business model has now made its way into the WordPress ecosystem as a way for attackers to profit from compromised WordPress websites and the computational resources of website visitors. It is imperative that WordPress site owners deploy a firewall and malware scan on their sites to quickly detect this new threat and ensure that their site visitors' resources are not hijacked to mine cryptocurrency.
What to Do If Your Site Is Infected With Cryptocurrency Mining MalwareThe most reliable way to recover if your website is hacked is to use our site cleaning service. Our team of experts will clean your site and get it back online as quickly as possible, and the service includes a detailed report and a 90-day guarantee. You can also use the Wordfence site security audit to do a comprehensive security inspection of your website.
If you prefer to try to fix any infection yourself, you can follow our guide to fixing a hacked website with Wordfence.
Did you enjoy this post? Share it!
4.90 (10 votes) Your rating:
Source: Cryptocurrency Miners Exploiting WordPress Sites
No comments:
Post a Comment