Continued from part 1 of our 5 part WordPress security series.
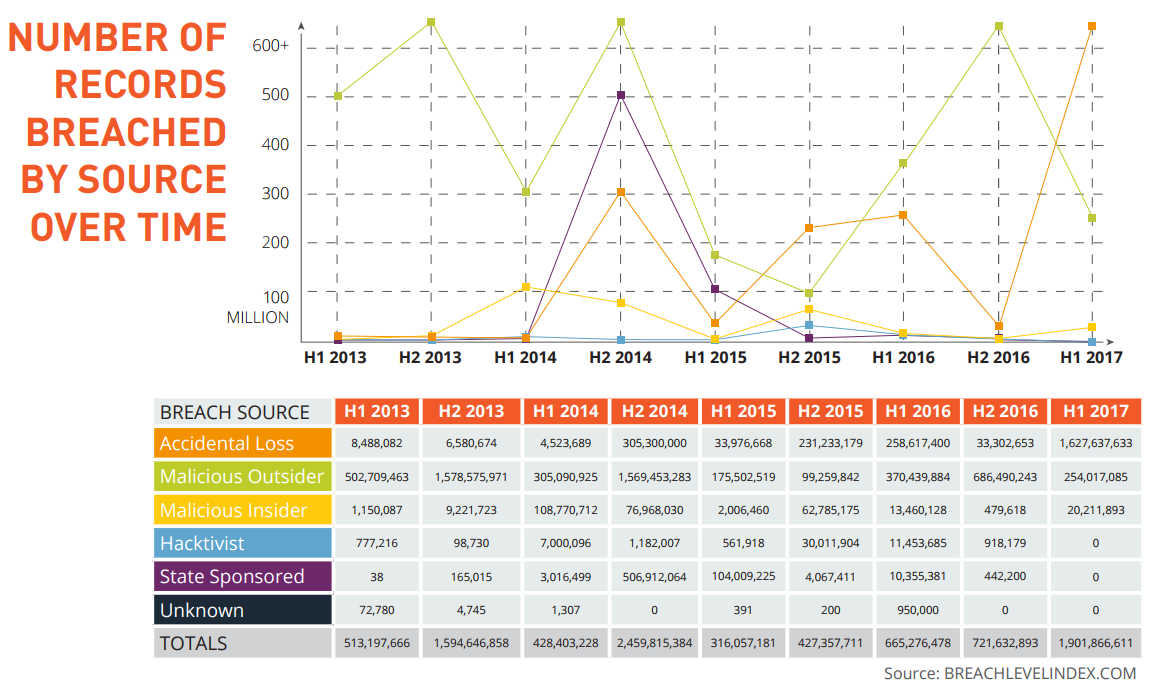
A recent Breach Level Index report by Gemalto, a global cyber security solutions provider, is titled "Poor Internal Security Practices Take A Toll" for a reason. The insider threat is the biggest source of stolen – or lost – records in the first half of 2017, according to the report. Accidental loss accounts for a whopping 86% of all stolen records, with over 1.6 billion records compromised in just six months.
Users prefer convenience over security because it's in human nature to look for easy ways to get a job done. So, if you want to boost your WordPress security, there is one potential threat that you can't afford to overlook – yourself and your users.
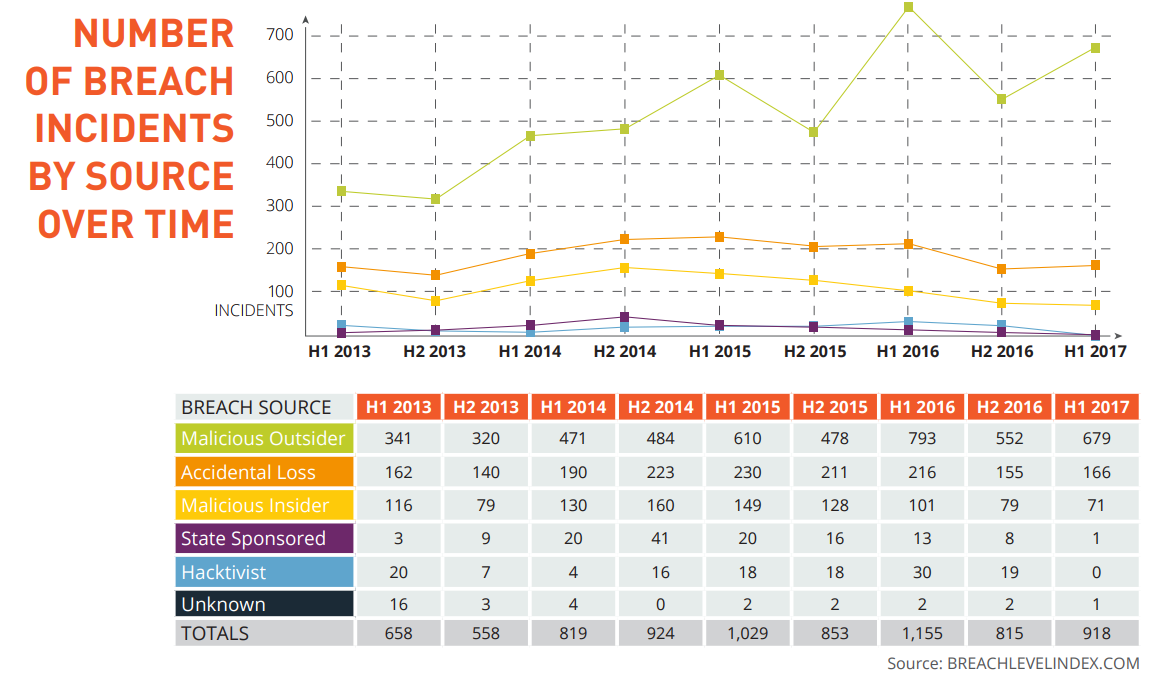
(Infographic Source: Breachlevelindex)
Contributors who have access to your WordPress back end can be a part of your defense, or your weakest link (without ever realizing it). Let's see how you can safeguard your blog against internal threats.
#1. Good Password HygieneWordPress – and common sense – requires that you use strong passwords, but what is a strong password? A WordPress expert Alex Grant says a strong password is complex and easy-to-memorize at the same time.
Password management programs do a great job of generating and storing your passwords in an orderly manner. This option is feasible if you have multiple blogs since you want to avoid re-using one password across multiple accounts.
Even though automatically generated passwords are secure, they are also impossible to memorize. So, many bloggers just default to weak passwords that are easy to crack.
One simple way of creating strong passwords you can memorize is to use a passphrase based on logic known to you alone, for instance:
My_goal_is_2_weigh_50_kilo$
The longer the passphrase, the harder it is to crack, and the easier it is to memorize. Use this technique not only for passwords but also for answers to your security questions.
Tips:One particular vulnerability that revolves around passwords is you can reset them. If someone gains access to your email, they can reset your WordPress password. If someone can guess – or research – the answers to your security questions, they can reset your password.
So, your password is just a part of the equation, where security of your administrative email account and reasonable complexity of your security answers are equally important.
#3. Locking Out Multiple Sign-On AttemptsAs of now, WordPress doesn't offer the functionality to block multiple sign-on attempts. This creates a risk for someone persistent enough to just try different username/password combinations for hours on end. So, you want to limit sign-on attempts to a certain number you deem acceptable.
Tips:For blogs with multiple contributors, it's best if the contributors only have privileges they need to do their work. You need to create the lowest risk environment, where user permissions are restricted to only the necessary minimum.
Otherwise, one user can mess up intentionally or accidentally, and delete someone else's post, or mishandle their login credentials and expose them.
If a contributor's account with minimum permissions gets compromised, the malicious party can only mingle with a very limited amount of content on your blog. If malicious actors access the administrative account, you're in for trouble.
Tip:If your contributors use weak passwords, your WordPress backend is vulnerable. Don't just leave your users to their own devices – set up restrictions that would only allow them to use strong passwords.
The current version of WordPress enforces the use of strong passwords. But if you run an older version, you can add this functionality via the Force Strong Passwords plugin.
Tips:One more security vulnerability that comes from users is they forget to log out. When they do, your blog is exposed to great risks. Anyone with access to your contributor's computer can tamper with your dashboard. So, security best practices suggest that you log out idle users.
Tip:That's it for today! The next WordPress security roundup will focus on:
So, stay tuned for more security tips from the WordPress guru Alex Grant.
Source: WordPress Security 101 – Protecting Against Insider Threats
No comments:
Post a Comment