This entry was posted in General Security, Research, Wordfence, WordPress Security on January 5, 2017 by Mark Maunder 14 Replies Visited 3,943 times, 3941 visits today
This week we are introducing something new. At the beginning of each month we will be doing a monthly WordPress security report. We will look at the attack data for the previous month from the 1st to the end of the month and provide a report and analysis on the attack activity we have seen on WordPress websites.
This is the monthly WordPress attack report from December 1st, 2016 until December 31st, 2016.
Most Active IPsIn the table below we have listed the most active attack IPs for December 2016. Note that the 'Attacks' column is in millions and is the total of all attacks that originated from each IP. Further right in the table (you may have to scroll) we break out the attacks into 'brute force' attacks and 'complex' attacks.
Brute force attacks are login guessing attacks. What we refer to as 'complex' attacks are attacks that were blocked by a rule in the Wordfence firewall.
We have also included the netblock owner which is the organization, usually a company, that owns the block of IP addresses that the attack IP belongs to. You can Google the name of the owner for more information. A Google search for any of these IP addresses frequently shows reports of attacks.
The hostname included is the PTR record (reverse DNS record) that the IP address owner created for their IP, so this is not reliable data but we include it for interest. For example, we have seen PTR records that claim the IP is a Tor exit node, but it is clearly not based on traffic.
We also include the country and a country flag. To the far right of the report we show the date in December we started logging attacks and the date attacks stopped. For many of these IPs we logged attacks for the entire month. For some you can see there is a clearly defined attack 'window' where the IP started and stopped.
The data below is embedded using a service called Airtable. This is the first time we're trying Airtable, so please leave your feedback in the comments. You'll note that it is also exportable.
Ukraine still owns the top spotAs you can tell from the table above, the Ukraine absolutely dominates the report. We have a total of 13 out of 25 top IPs that are based in Ukraine. Attacks are originating from 4 Ukrainian netblock owners:
Surprisingly, France takes the number 2 spot for the most IPs in the top 25 list with a total of 7 attack IPs. Most of these originate from Iliad Enterprises. Iliad is a large organization with many subsidiaries and over 4000 employees. They tried to buy T-Mobile in the USA 2 years ago. The netblock for these IPs is registered to Iliad, but the attacks may originate from one of many subsidiaries of Iliad, like the ISP 'Free' in France.
Seychelles
The outlier on the map is an IP address "89.248.172.121" based in Seychelles, which is an island off the east coast of Africa. Seychelles has a population of just over 90,000 and is officially the smallest sovereign African nation.
We logged 2.2 million complex attacks originating in Seychelles. This is surprising because internet access to islands is generally expensive and slow. But Seychelles is doing their part to contribute to global attacks on WordPress publishers.
We tracked the attacks to what appears to be an audio-visual store in downtown Victoria in Seychelles, based on public whois information for this IP. The IP is not a known Tor exit node and it probably is not a VPN exit node because it is unlikely that Seychelles has their own VPN provider.
Based on usage patterns we are seeing available in public data (try a Google search), the IP appears to be the public IP for users of a local Seychelles ISP. The attacks are probably an individual based in Victoria, Seychelles, who is using the ISP.
Complex Attacks vs Brute Force AttacksA brute force attack is a password guessing attack that is simplistic and has a low likelihood of success. At Wordfence we consider a 'complex' attack to be an attack that tries to exploit a vulnerability in WordPress or a WordPress plugin. If you are using Wordfence to protect your WordPress website, brute force attacks are blocked by our brute-force protection and complex attacks are blocked by the Wordfence firewall.
The top two IPs, one in Ukraine and one in Russia, are both using complex attacks to target WordPress websites. They are also launching far more attacks than the top brute force attacker. They launched 32 and 12 million attacks respectively, while the top brute force attacker only launched 6.3 million attacks.
However, if you look at the total attacks we saw for the top 25 IP addresses, we saw 63 million complex attacks and 67 million brute force attacks. The most active IPs are choosing to launch complex attacks that are blocked by the Wordfence firewall, but the most common attack type is brute force, or password guessing.
This makes sense because more sophisticated attackers will launch a high volume of attacks that will have a high success rate. They will therefore choose to launch complex attacks and a huge number of them. Less sophisticated attackers will launch brute force attacks but won't be able to deliver the same attack volume as the pros. So you should see a lot of lower volume IPs engaging in brute force attacks and a few high volume IPs engaging in complex attacks, and that's exactly what we are seeing.
What, no Tor?Something that we noticed in this report that we did not include in the table is the number of Tor exit nodes in the top 25 attack IPs. There are none. In our full dataset, we can see a large number of Tor exit nodes. We identify them from a list of Tor exit nodes and in every single case, both complex and brute-force attacks originate from the exit node.
In the top 25 list, not a single IP is a Tor exit node. Tor exit nodes are probably used by several low volume attackers for a wide variety of attacks. Using Tor is anonymous, but slow. Tor introduces a lot of latency (delay) in web requests. When you decide to bulk hack millions of WordPress websites, you probably don't want the latency that comes with using Tor. You can learn more about Tor in our Learning Center.
Brute Force AttacksIf you recall our post on December 16th where we described a "Huge Increase in brute force attacks in December", we saw a marked increase in the number of attacked sites starting in late November. We also saw the number of attacks gradually increase above our 60 day average, peaking at just over 2o million attacks per day. And finally around the 16th of December was saw a dramatic spike in the number of attack IPs engaging in brute force attacks. Reference the original brute force post for those charts.
Now that we have the full data for December, you can see that this culminated in a huge increase in total attacks at the end of the month.
In late December we saw a massive spike in brute force attacks. The average for the month was 20 million attacks per day, and the total attacks we blocked spiked to over 45 million for a period of 48 hours.
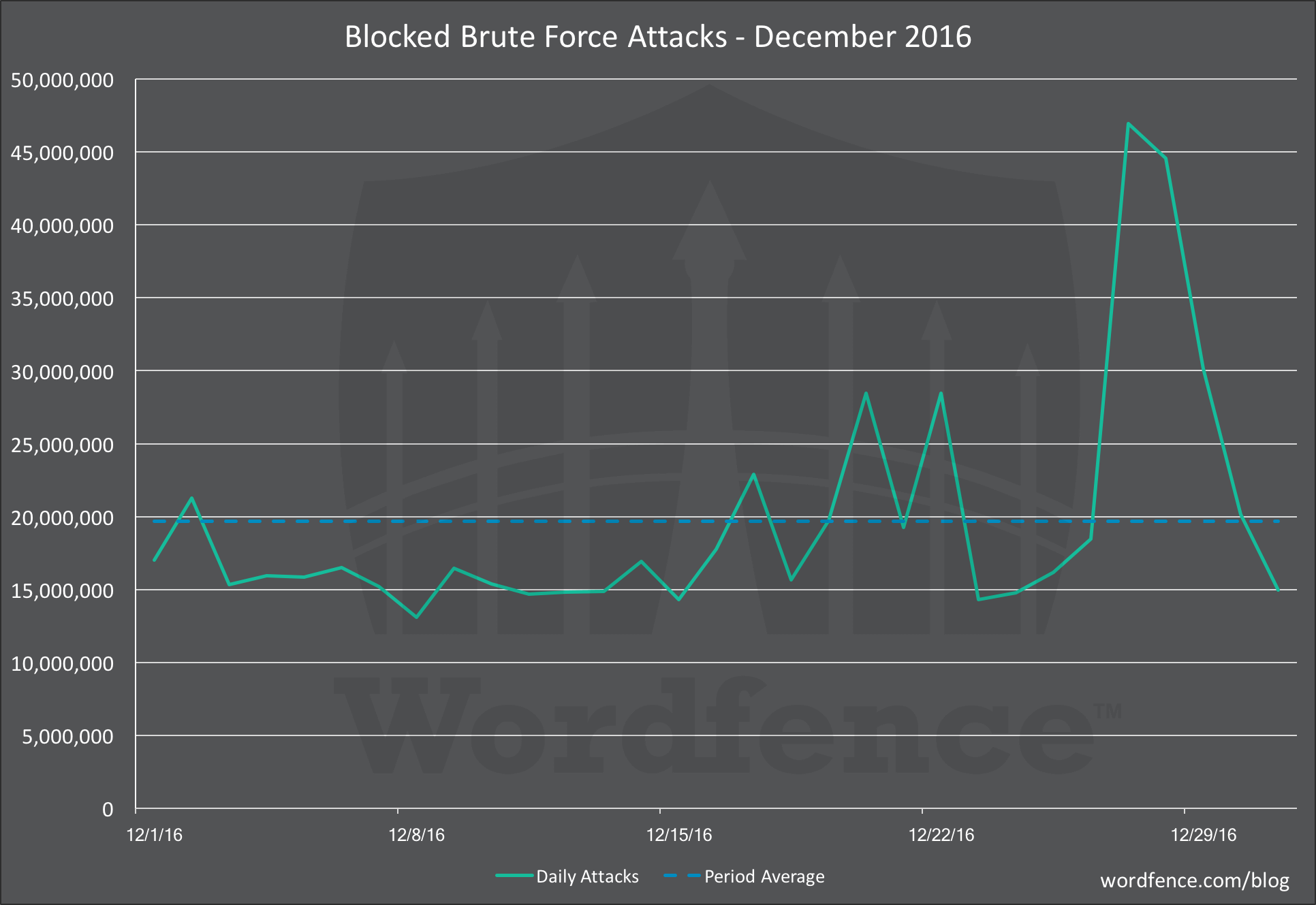
As you can tell from our top 25 data, no single IP generated more than 6.3 million brute force attacks for the entire period. To add an additional 25 million attacks per day, over and above what we normally see, an attacker would have to compromise a large number of IP addresses and then launch attacks distributed across their new attack platform. The data from our mid-month report showed that large spike in new attack IPs.
The attack quickly died down and this may have been due to the noise the attacking IPs were generating. It would have been easy for hosting providers to detect outgoing malicious activity on their networks and shut down the servers that were launching these attacks.
Early this month we have seen brief spikes of similar activity that have lasted a few hours. We have not yet seen a multi-day effort like we saw in late December.
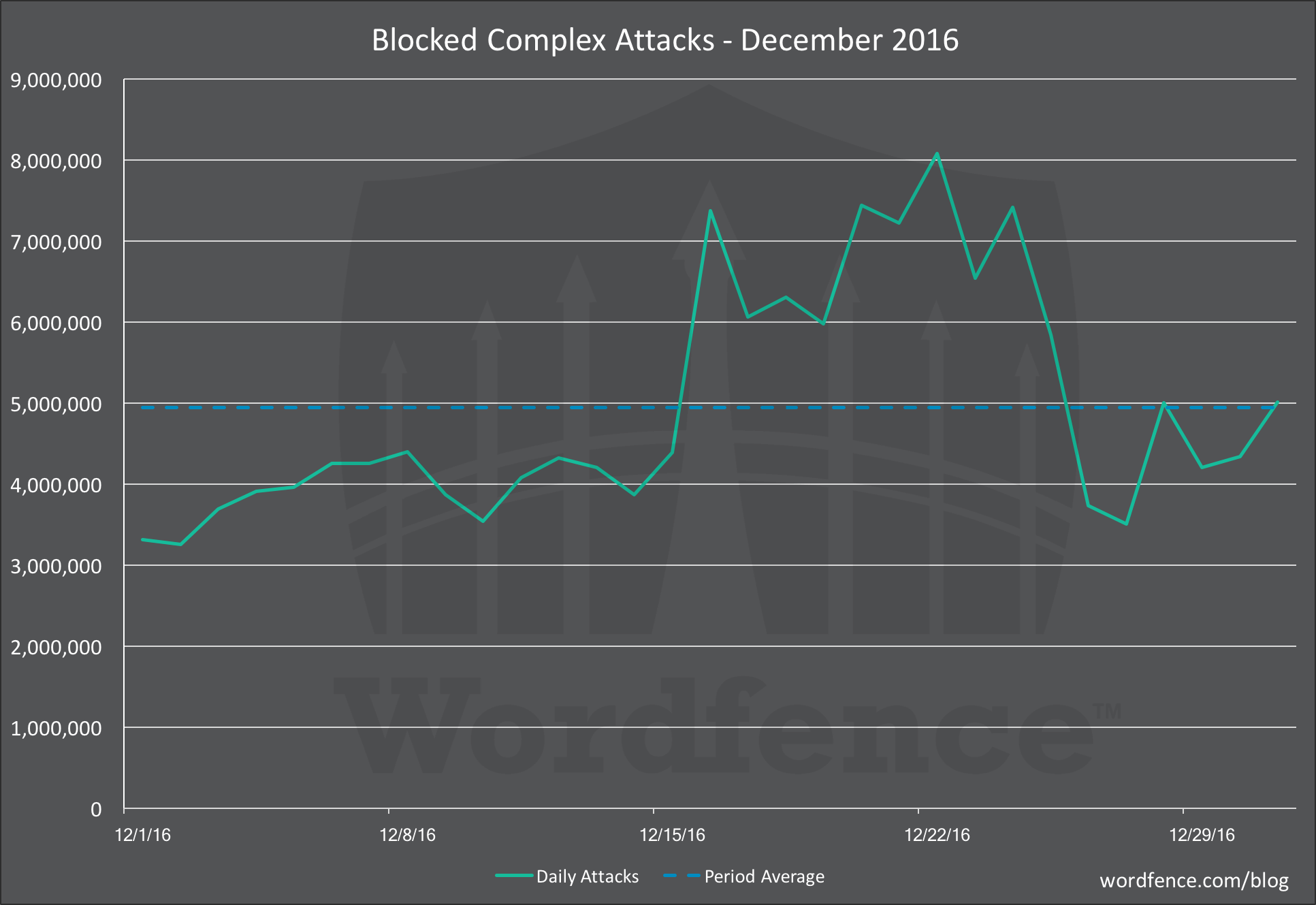
Complex AttacksFrom December 15th to December 27th we saw a marked increase in complex attacks that were blocked by the Wordfence firewall. Attack volume did not quite double, as we saw in the brute force chart above.
The peak attack volume for complex attacks blocked by Wordfence was just over 8 million attacks per day. There is no strong correlation in the timing of complex attacks and brute force attacks or the duration. They appear to be disconnected.
The table below shows which plugins were most targeted by attacks in December 2016. You should note that all of these are publicly known vulnerabilities that the plugin vendor is probably aware of and has fixed, although we have not verified this.
The list below is simply a list of what we are seeing attacked in the wild. It is not a list of "most vulnerable" plugins or a list of plugins that are currently vulnerable.
The "Plugin Slug" is the unique 'slug' used to identify the plugin to WordPress. It is easier for us to extract plugins by 'slug' from our attack data than get actual plugin names.
Each plugin has a link to a vulnerability report that is likely the vulnerability being exploited in each case. (Click the slug) We have also included the year the vulnerability was published next to the slug.
You'll notice that many of these are old vulnerabilities. Some of them date as far back as 2012. The reason we think these old vulnerabilities are being so widely exploited is because most attacks use free, off-the-shelf WordPress scan and exploit tools.
These tools come pre-loaded with a number of exploits that an inexperienced attacker can automatically launch at any WordPress website. This makes up the bulk of the attacks on WordPress plugins that we see. They have a low likelihood of success if you are keeping your WordPress installation up-to-date.
Rank Plugin Slug Attacks Blocked 1 google-mp3-audio-player (2014) 3,866,201 2 db-backup (2014) 3,607,072 3 wp-symposium (2015) 1,635,894 4 dzs-zoomsounds (2015) 1,617,512 5 really-simple-guest-post (2015) 1,230,015 6 wp-ecommerce-shop-styling (2015) 1,123,328 7 candidate-application-form (2015) 1,117,750 8 tinymce-thumbnail-gallery (2012) 1,043,966 9 pica-photo-gallery (2012) 1,023,009 10 plugin-newsletter (2012) 1,011,422 11 simple-download-button-shortcode (2012) 986,659 12 dukapress (2014) 946,831 13 wp-filemanager (2013) 909,217 14 jquery-html5-file-upload (2016) 883,365 15 recent-backups (2015) 847,996 16 simple-ads-manager (2015) 825,505 17 wpshop (2015) 775,787 18 aviary-image-editor-add-on-for-gravity-forms (2015) 774,018 19 acf-frontend-display (2015) 771,248 20 formcraft (2016) 764,899 21 work-the-flow-file-upload (2015) 757,809 22 woocommerce-product-options (2016) 757,531 23 wptf-image-gallery (2015) 752,382 24 inboundio-marketing (2015) 751,198 25 front-end-upload (2012) 745,027 Themes seeing the most attacksThe list below shows the slugs of themes that we saw most commonly targeted in December 2016. Once again, this is not a list of vulnerable themes or the 'most unsafe' themes. They are simply commonly targeted and most likely had vulnerabilities at some point that have now been fixed.
We've included the year each vulnerability that is being exploited was published and most of the slugs in the table have links to the exploit that is most likely being used.
As with the plugins, this list contains many old exploits, probably for the same reason. Most of the vulnerabilities in this list are "local file inclusion" vulnerabilities that allow an attacker to download wp-config.php or other sensitive files.
Rank Theme Slug Attacks 1 mTheme-Unus (2015) 3,485,508 2 churchope (2014) 3,399,433 3 lote27 (2014) 2,566,892 4 elegance (2014) 1,840,865 5 awake (2016) 1,838,267 6 infocus (2014) 1,830,555 7 echelon (2014) 1,386,527 8 dejavu (possibly 2014) 1,310,259 9 construct (unknown) 1,155,775 10 fusion (2015) 1,147,655 11 persuasion (2013) 1,128,816 12 method (unknown) 1,110,563 13 myriad (unknown) 1,099,149 14 infocus2 (2015) 1,096,006 15 parallelus-mingle (unknown) 1,084,646 16 trinity (2014) 1,083,314 17 urbancity (2014) 1,081,411 18 epic (2014) 1,078,927 19 parallelus-salutation (2015) 1,067,890 20 modular (unknown) 1,067,402 21 linenity (2014) 1,063,945 22 authentic (2014) 1,043,639 23 antioch (2014) 981,204 24 NativeChurch (2015) 891,350 25 estrutura-basica (2015) 451,997 ConclusionThat concludes our monthly attack report for December 2016. You are welcome to download the top 25 list of IP addresses and perform your own analysis. The Airtable embed includes an option for a CSV download.
We welcome to share your own findings in the comments and any questions you might have.
Mark Maunder – Wordfence Founder/CEO.
Did you enjoy this post? Share it!
4.84 (19 votes) Your rating:
Source: The December 2016 WordPress Attack Activity Report
No comments:
Post a Comment